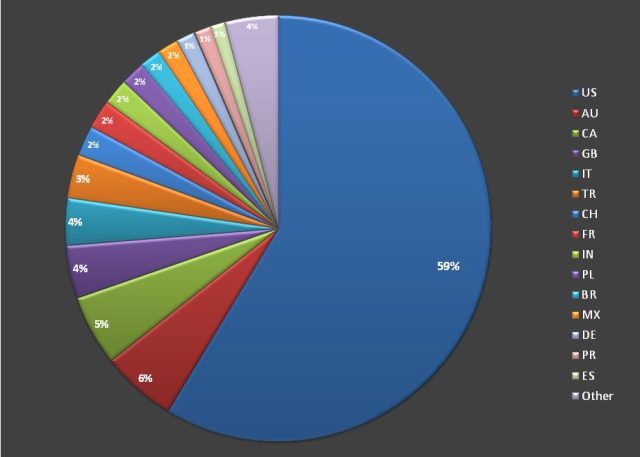
This is related to our initial post about the PHP.net attack and whether or not the source code was compromised. According to this article, “One of five distinct malware types served to visitors of php.net from October 22 to October 24, DGA.Changer employs a novel way of evading detection and takedown attempts.”




