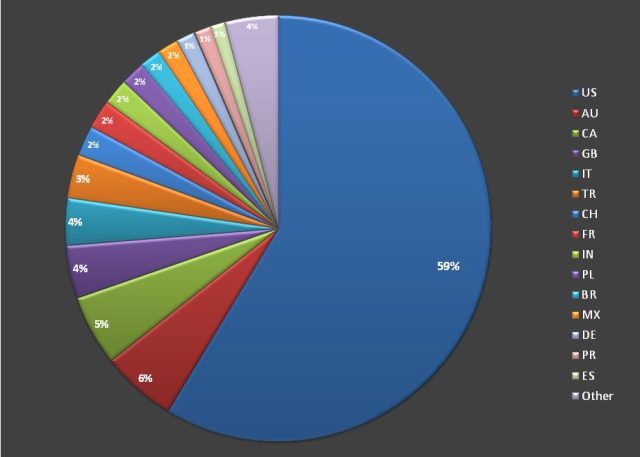
Linkedin is ripe with information about people. In a targeted attack, facebook and linkedin would probably be the two places to start gathering information. Many people lock down facebook, but Linkedin doesn’t have the same privacy controls and in fact, often times the information on linkedin is meant to be public. What linkedin provides is a free, centralized source for that information.
Source: http://securityaffairs.co/wordpress/19446/cyber-crime/linkedin-targeted-attacks.html